【Lab Objectives】
1. Master the VTP configuration methods.
2. Master the routing configuration methods between VLANs and the sub-interface configurations.
【Lab Topology】
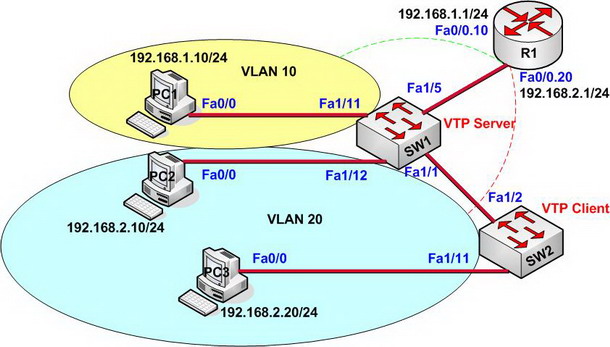
【Lab Steps】
1. Configure PC1、PC2 and PC3 to be used as simulation hosts, the configuration is as follows
|
PC1(config)#no ip routing PC1(config)# PC1(config)#ip default-network 192.168.1.1 PC1(config)# PC1(config)#interface fastEthernet 0/0 PC1(config-if)#ip address 192.168.1.10 255.255.255.0 PC1(config-if)#no shutdown PC1(config-if)#exit PC1(config)# |
|
PC2(config)#no ip routing PC2(config)# PC2(config)#ip default-network 192.168.2.1 PC2(config)# PC2(config)#interface fastEthernet 0/0 PC2(config-if)#ip address 192.168.2.10 255.255.255.0 PC2(config-if)#no shutdown PC2(config-if)#exit PC2(config)# |
|
PC3(config)#no ip routing PC3(config)# PC3(config)#ip default-network 192.168.2.1 PC3(config)# PC3(config)#interface fastEthernet 0/0 PC3(config-if)#ip address 192.168.2.20 255.255.255.0 PC3(config-if)#no shutdown PC3(config-if)#exit PC3(config-if)# |
2. Configure trunk between SW1 and SW2, the configuration is as follows:
|
SW1(config)#interface fastEthernet 1/1 SW1(config-if)#switchport trunk encapsulation dot1q SW1(config-if)#switchport mode trunk SW1(config-if)#exit |
|
SW2(config)#interface fastEthernet 1/2 SW2(config-if)#switchport trunk encapsulation dot1q SW2(config-if)#switchport mode trunk SW2(config-if)#exit |
3. Check the trunk information:
|
SW2#show interfaces trunk
Port Mode Encapsulation Status Native vlan Fa1/2 on 802.1q trunking 1
Port Vlans allowed on trunk Fa1/2 1-1005
Port Vlans allowed and active in management domain Fa1/2 1
Port Vlans in spanning tree forwarding state and not pruned Fa1/2 1 SW2# |
4. Check the VTP status of SW1 and SW2 before configuring VTP
|
SW2#show vtp status VTP Version : 2 Configuration Revision : 0 Maximum VLANs supported locally : 256 Number of existing VLANs : 5 VTP Operating Mode : Server VTP Domain Name : VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0xBF 0x86 0x94 0x45 0xFC 0xDF 0xB5 0x70 Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00 Local updater ID is 0.0.0.0 (no valid interface found) |
5. Configure VTP on SW1 and SW2
|
SW1#vlan database SW1(vlan)#vtp domain ccnp Changing VTP domain name from NULL to ccnp SW1(vlan)# SW1(vlan)#vtp server Device mode already VTP SERVER. SW1(vlan)# SW1(vlan)#vtp password cisco Setting device VLAN database password to cisco. SW1(vlan)# SW1(vlan)#vtp pruning SW1(vlan)# |
6. Configure VTP in the global configuration mode.
|
SW2(config)#vtp password cisco Setting device VLAN database password to cisco SW2(config)# SW2(config)#vtp domain ccnp Changing VTP domain name from fuckcisco to ccnp SW2(config)# SW2(config)#vtp pruning Pruning switched on SW2(config)# SW2(config)#vtp mode client Setting device to VTP CLIENT mode. SW2(config)# |
7. Check the information about VTP status on SW1 and SW2
|
SW2#show vtp status VTP Version : 2 Configuration Revision : 1 Maximum VLANs supported locally : 1005 Number of existing VLANs : 10 VTP Operating Mode : Client VTP Domain Name : ccnp VTP Pruning Mode : Enabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0x71 0x62 0x0B 0xD1 0xED 0xFD 0x7D 0xAC Configuration last modified by 199.1.1.3 at 3-2-93 02:11:08 SW2# |
8. Create VLAN on SW1 and SW2
|
SW1#vlan database SW1(vlan)#vlan 10 name cisco VLAN 10 added: Name: cisco SW1(vlan)#exit APPLY completed. Exiting…. SW1# SW1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# SW1(config)#vlan 20 SW1(config-vlan)#name microsoft SW1(config-vlan)#exit |
9. Check the VLAN configuration on SW1
|
SW1#show vlan
VLAN Name Status Ports ——————————————— ——————————- 1 default active Fa1/0, Fa1/2, Fa1/3, Fa1/4 Fa1/5, Fa1/6, Fa1/7, Fa1/8 Fa1/9, Fa1/10, Fa1/11, Fa1/12 Fa1/13, Fa1/14, Fa1/15 10 cisco active 20 microsoft active 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 —- —– ———- —– —— —— ——– —- ——– —— —— 1 enet 100001 1500 – – – – – 1002 1003 10 enet 100010 1500 – – – – – 0 0 20 enet 100020 1500 – – – – – 0 0 1002 fddi 101002 1500 – – – – – 1 1003 1003 tr 101003 1500 1005 0 – – srb 1 1002 1004 fdnet 101004 1500 – – 1 ibm – 0 0 1005 trnet 101005 1500 – – 1 ibm – 0 0 SW1# |
10. Check the VTP status information.
|
SW1#show vtp status VTP Version : 2 Configuration Revision : 2 Maximum VLANs supported locally : 256 Number of existing VLANs : 7 VTP Operating Mode : Server VTP Domain Name : ccnp VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0xF3 0x1C 0x33 0x46 0xEA 0x14 0xBB 0x9F Configuration last modified by 0.0.0.0 at 3-1-02 00:52:53 Local updater ID is 0.0.0.0 (no valid interface found) SW1# |
11. Check the VTP status information on SW2.
|
SW2#show vtp status VTP Version : 2 Configuration Revision : 2 Maximum VLANs supported locally : 256 Number of existing VLANs : 7 VTP Operating Mode : Client VTP Domain Name : ccnp VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0xF3 0x1C 0x33 0x46 0xEA 0x14 0xBB 0x9F Configuration last modified by 0.0.0.0 at 3-1-02 00:52:53 SW2# |
12. Check the VLAN information on SW2.
|
SW1#show vlan
VLAN Name Status Ports ——————————————— ——————————- 1 default active Fa0/3, Fa0/4, Fa0/5, Fa0/6 Fa0/7, Fa0/8, Fa0/9, Fa0/10 Fa0/11, Fa0/12, Fa0/13, Fa0/14 Fa0/15, Fa0/16, Fa0/17, Fa0/18 Fa0/19, Fa0/20, Fa0/21, Fa0/22 Fa0/23, Fa0/24, Gi0/1, Gi0/2 10 cisco active 20 microsoft active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup ………… |
13. Add the appropriate host ports into the VLAN on SW1 and SW2.
|
SW1(config)#interface fastEthernet 1/11 SW1(config-if)#switchport access vlan 10 SW1(config-if)#exit SW1(config)# SW1(config)#interface fastEthernet 1/12 SW1(config-if)#switchport access vlan 20 SW1(config-if)#exit |
14. Configure VLAN on SW2
|
SW2(config)#interface fastEthernet 1/11 SW2(config-if)#switchport access vlan 20 SW2(config-if)#exit |
15. Use the ping command on PC1, PC2 and PC3 to test communications between VLANs.
|
PC1#ping 192.168.1.20
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.20, timeout is 2 seconds: ….. Success rate is 0 percent (0/5) PC1# |
|
PC2#ping 192.168.2.20
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.20, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 24/24/24 ms PC2# PC2#ping 192.168.1.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.10, timeout is 2 seconds: ….. Success rate is 0 percent (0/5) PC2# |
|
PC3#ping 192.168.2.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/18/32 ms PC3# PC3#ping 192.168.1.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.10, timeout is 2 seconds: ….. Success rate is 0 percent (0/5) |
16. Configure single-arm routing on R1 to guarantee the communication between two VLANs.
17. Configure the TRUNK link between R1 and SW1, the configuration is as follows:
|
SW1(config)#interface fastEthernet 1/5 SW1(config-if)#switchport trunk encapsulation dot1q SW1(config-if)# SW1(config-if)#switchport mode trunk SW1(config-if)#exit |
|
R1(config)# R1(config)#interface fastEthernet 0/0 R1(config-if)#no ip address R1(config-if)#no shutdown R1(config-if)#exit R1(config)# R1(config)#interface fastEthernet 0/0.10 R1(config-subif)#encapsulation dot1Q 10 R1(config-subif)#ip address 192.168.1.1 255.255.255.0 R1(config-subif)#exit R1(config)# R1(config)#interface fastEthernet 0/0.20 R1(config-subif)#encapsulation dot1Q 20 R1(config-subif)#ip address 192.168.2.1 255.255.255.0 R1(config-subif)#exit R1(config)# |
18. Check the R1 routing table.
|
R1#show ip route
Gateway of last resort is not set
C 192.168.1.0/24 is directly connected, FastEthernet0/0.10 C 192.168.2.0/24 is directly connected, FastEthernet0/0.20 |
19. Use the ping command on PC1, PC2 and PC3 to test routes between VLANs.
|
PC1#ping 192.168.1.1
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/232/1040 ms PC1# PC1#ping 192.168.2.1
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/223/1012 ms PC1# PC1#ping 192.168.2.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.10, timeout is 2 seconds: ..!!! Success rate is 60 percent (3/5), round-trip min/avg/max = 12/48/92 ms PC1# PC1#ping 192.168.2.20
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.20, timeout is 2 seconds: ..!!! Success rate is 60 percent (3/5), round-trip min/avg/max = 20/52/96 ms |
|
PC2#ping 192.168.1.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/48/88 ms |
|
PC3#ping 192.168.1.10
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 12/50/88 ms |
20. End.
Hope to helpful for you!




