1. A network administrator needs to force a high-performance switch that is located in the MDF to become the root bridge for a redundant path switched network. What can be done to ensure that this switch assumes the role as root bridge?
A: Establish a direct link from the switch to all other switches in the network.
B: Assign the switch a higher MAC address than the other switches in the network have.
C: Configure the switch so that it has a lower priority than other switches in the network.
D: Configure the switch for full-duplex operation and configure the other switches for half-duplex operation.
E: Connect the switch directly to the MDF router, which will force the switch to assume the role of root bridge.
Correct Answers: C
Explanation:
For all switches in a network to agree on a loop-free topology, a common frame of reference must exist. This reference point is called the Root Bridge. The Root Bridge is chosen by an election process among all connected switches. Each switch has a unique Bridge ID (also known as the bridge priority) that it uses to identify itself to other switches. The Bridge ID is an 8-byte value. 2 bytes of the Bridge ID is used for a Bridge Priority field, which is the priority or weight of a switch in relation to all other switches.
The other 6 bytes of the Bridge ID is used for the MAC Address field, which can come from the Supervisor module, the backplane, or a pool of 1024 addresses that are assigned to every Supervisor or backplane depending on the switch model. This address is hard coded, unique, and cannot be changed.
The election process begins with every switch sending out BPDUs with a Root Bridge ID equal to its own Bridge ID as well as a Sender Bridge ID. The latter is used to identify the source of the BPDU message. Received BPDU messages are analyzed for a lower Root Bridge ID value. If the BPDU message has a Root Bridge ID (priority) of the lower value than the switch’s own Root Bridge ID, it replaces its own Root Bridge ID with the Root Bridge ID announced in the BPDU. If two Bridge Priority values are equal, then the lower MAC address takes preference.
2. Which protocol provides a method of sharing VLAN configuration information between switches?
A: VTP
B: STP
C: ISL
D: 802.1Q
E: VLSM
Correct Answers: A
Explanation:
VLAN Trunking Protocol (VTP) is a Cisco proprietary Layer 2 messaging protocol that manages the addition, deletion, and renaming of VLANs on a network-wide basis. Virtual Local Area Network (VLAN) Trunk Protocol (VTP) reduces administration in a switched network. When you configure a new VLAN on one VTP server, the VLAN is distributed through all switches in the domain. This reduces the need to configure the same VLAN everywhere. To do this VTP carries VLAN information to all the switches in a VTP domain. VTP advertisements can be sent over ISL, 802.1q, IEEE 802.10 and LANE trunks. VTP traffic is sent over the management VLAN (VLAN1), so all VLAN trunks must be configured to pass VLAN1. VTP is available on most of the Cisco Catalyst Family products.
3.Which statement accurately describes a benefit provided by VTP?
A: VTP allows routing between VLANs.
B: VTP allows a single port to carry information to more than one VLAN.
C: VTP allows physically redundant links while preventing switching loops.
D: VTP allows switches to share VLAN configuration information.
Correct Answers: D
Explanation:
Trunking Protocol (VTP) are to manage all configured VLANs across a switched internetwork and to maintain consistency throughout that network VTP allows you to add, delete, and rename VLANs-information that is then propagated to all other switches in the VTP domain.
Here’s a list of some features of VTP:
* Consistent VLAN configuration across all switches in the network
* VLAN trunking over mixed networks, such as Ethernet to ATM LANE or even FDDI
* Accurate tracking and monitoring of VLANs
* Dynamic reporting of added VLANs to all switches in the VTP domain
* Plug and Play VLAN adding
4. Which two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.)
A:amount of RAM
B:bridge priority
C:IOS version
D:IP address
E:MAC address
F:speed of the links
Correct Answers: B, E
Explanation:
The bridges elect a root bridge based on the bridge IDs in the BPDUs. The root bridge is the bridge with the lowest numeric value for the bridge ID. Because the two part bridge ID starts with the priority value, essentially the bridge with the lowest priority becomes the root. For instance, if one bridge has priority 100, and another bridge has priority 200, the bridge with priority 100 wins, regardless of what MAC address was used to create the bridge ID or each bridge/switch.
5. In which Spanning-Tree states does a switch port learn MAC addresses? (Choose two)
A. Blocking
B. Listening
C. Forwarding
D. Learning
Correct Answers: C, D
Explanation:
STP uses a couple of port states besides forwarding and blocking.
1. Listening – Listens to incoming Hello messages to ensure that there are no loops, but does not forward traffic. This is an interim state between blocking and forwarding.
2. Learning – Still listens to BPDUs, plus learns MAC addresses from incoming frames. It does not forward traffic. This is an interim state between blocking and forwarding.
3. Disabled – Administratively down.
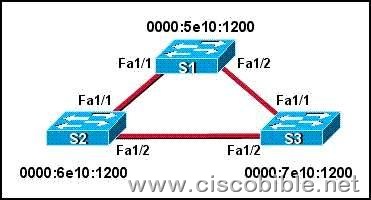
6. Refer to the exhibit. All switches have the default STP configuration and all links are Fast Ethernet. Which port on which switch will Spanning Tree place in blocking mode?
A: Switch S1 – Port Fa1/1
B: Switch S1 – Port Fa1/2
C: Switch S2 – Port Fa1/2
D: Switch S2 – Port Fa1/1
E: Switch S3 – Port Fa1/2
F: Switch S3 – Port Fa1/1
Correct Answers: E
Explanation:
Switch S1 will become the ROOT BRIDGE because it has the lowest MAC address.
Its both ports will become designated ports so choice A and B are wrong.
Next Election will be of ROOT PORTS. Port FA1/1 of both the switches S2 and S3 will become ROOT ports because they have minimum path cost to reach the root bridge.
So, choices D and E are also wrong.
Next Election will be of Designated Ports on the segment connecting S2 and S3. S2 has lower MAC address so, its port FA1/2 will become designated port and FA1/2 of S3 will be placed in a BLOCKING state to avoid switching LOOPS.
7. What is the purpose of Spanning Tree Protocol?
A: to prevent routing loops
B: to create a default route
C: to provide multiple gateways for hosts
D: to maintain a loop-free Layer 2 network topology
E: to enhance the functions of SNMP
Correct Answers: D
Explanation:
STP’s main task is to stop network loops from occurring on your Layer 2 network (bridges or switches). It vigilantly monitors the network to find all links, making sure that no loops occur by shutting down any redundant ones. STP uses the spanning-tree algorithm (STA) to first create a topology database, then search out and destroy redundant links. With STP running, frames will only be forwarded on the premium, STP-picked links.