1. Why does the data communication industry use the layered OSI reference model? (Choose two.)
A:It divides the network communication process into smaller and simpler components, thus aiding component development, design, and troubleshooting.
B:It enables equipment from different vendors to use the same electronic components, thus saving research and development funds.
C:It supports the evolution of multiple competing standards, and thus provides business opportunities for equipment manufacturers.
D:It encourages industry standardization by defining what functions occur at each layer of the model.
E:It provides a means by which changes in functionality in one layer require changes in other layers.
Correct Answers: A, D
Explanation:
The OSI (Open System Interconnection) reference model was created as a reference point for communications devices. A layered approach is used to segment the entire telecommunications process into a series of smaller steps. A is correct because it encourages a level of standardization by encouraging that functions be compared to known layers. D is also correct because it allows engineers to focus on the development, refining, and perfection of simpler components.
2. Which of the following are types of flow control? (Choose three.)
A:buffering
B:cut-through
C:windowing
D:congestion avoidance
E:load balancing
Correct Answers: A, C, D
3.Which of the following services use UDP? (Choose three.)
A:DNS
B:Telnet
C:SMTP
D:SNMP
E:HTTP
F:TFTP
Correct Answers: A, D, F
Explanation:
The most often used port numbers of TCP/UDP are as follows:
The port numbers of TCP:
20 FTP data
21 FTP control
23 Telnet
25 SMTP
53 DNS
80 WWW
100 POP3
The port numbers of UDP
53 DNS
69 TFTP
161 SNMP
Note: DNS uses TCP to perform Zone Transfers and UDP to query name.
The ACL created on the router denied the traffic from the ports 21,23,25, thus allowing these three types of traffic such as DNS, POP3, HTTP to cross .
4.Which of the following are associated with the application layer of the OSI model? (Choose two.)
A:ping
B:Telnet
C:FTP
D:TCP
E:IP
Correct Answers: B, C
5.Which of the following services use TCP? (Choose three.)
A:DHCP
B:SMTP
C:SNMP
D:FTP
E:HTTP
F:TFTP
Correct Answers: B, D, E
Explanation:
TCP (Transmission Control Protocol) is a reliable mechanism for data delivery. SMTP, FTP and HTTP services use TCP via ports 25, 20/21, and 80, respectively.
6. What is the purpose of an ARP request message?
A: It binds the IP address of a host to the network that it is on.
B: It builds a correlation between an IP address and a MAC address.
C: It provides connectivity and path selection between hosts on a network.
D: It encapsulates the Layer 3 address and then passes the packet to Layer 2.
E: It creates a session by passing a header with the destination Layer 2 address to the transport layer.
Correct Answers: B
Explanation:
Address Resolution Protocol (ARP) finds the hardware address of a host from a known IP address. When IP has a datagram to send, it must inform a Network Access protocol, such as Ethernet or Token Ring, of the destination’s hardware address on the local network. (It has already been informed by upper-layer protocols of the destination’s IP address.) If IP doesn’t find the destination host’s hardware address in the ARP cache, it uses ARP to find this information.
This is the protocol operates on Network Layer. Source device sends the ARP broadcast to resolve the MAC address of destination device.
You can display the ARP table using the "show arp" command.
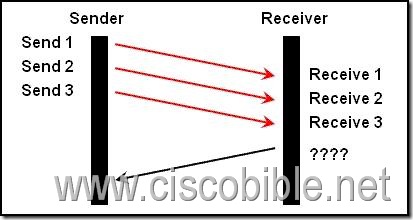
7. A TCP/IP transfer is diagrammed in the exhibit.
A window size of three has been negotiated for this transfer. Which message will be returned from the receiver to the sender as part of this TCP/IP transfer?
A: send ACK 1-3
B: send ACK 3
C: send ACK 4
D: send ACK 4-6
E: send ACK 6
F: send ACK 7
Correct Answers: C
Explanation:
TCP is knows as a reliable service. Reliable data delivery ensures the integrity of a stream of data sent from one machine to the other through a fully functional data link. It guarantees that the data won’t be duplicated or lost. This is achieved through something called positive acknowledgment with retransmission a technique that requires a receiving machine to communicate with the transmitting source by sending an acknowledgment message back to the sender when it receives data.
The sender documents each segment it sends and waits for this acknowledgment before sending the next segment. When it sends a segment, the transmitting machine starts a timer and retransmits if it expires before an acknowledgment is returned from the receiving end. In this case, 3 segments were received, so the receiver sends back an ACK value of 4 as it is expecting the 4th segment next.





It’s cooollll………..
& helpfull 2 all