OSPF Lab2 - Configuring OSPF Authentication
【Lab Objectives】
Learn configuration methods of OSPF interface authentication and area authentication.
【Lab Topology】
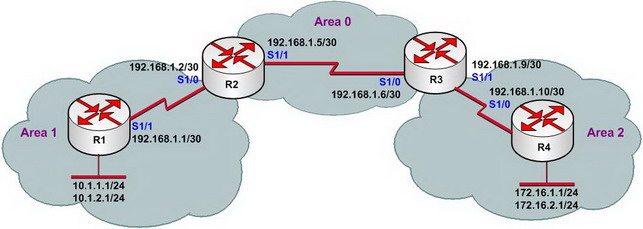
【Lab Steps】
1. Configure IP addresses of every router, and use ping command to confirm the direct interface connectivity of every router.
2. Configure OSPF protocol, and use related commands to confirm that it can cork normally
3. Check routing table of R1 and R2.
R1#show ip route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 2 subnets
O IA 172.16.1.0 [110/193] via 192.168.1.2, 00:01:02, Serial1/1
O IA 172.16.2.0 [110/193] via 192.168.1.2, 00:01:02, Serial1/1
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback0
C 10.1.1.0 is directly connected, Loopback1
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:01:12, Serial1/1
C 192.168.1.0 is directly connected, Serial1/1
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:05:47, Serial1/1
R1#
|
R2#show ip route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 2 subnets
O IA 172.16.1.0 [110/129] via 192.168.1.6, 00:09:16, Serial1/1
O IA 172.16.2.0 [110/129] via 192.168.1.6, 00:09:16, Serial1/1
10.0.0.0/24 is subnetted, 2 subnets
O 10.1.2.0 [110/65] via 192.168.1.1, 00:14:00, Serial1/0
O 10.1.1.0 [110/65] via 192.168.1.1, 00:14:00, Serial1/0
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/128] via 192.168.1.6, 00:09:26, Serial1/1
C 192.168.1.0 is directly connected, Serial1/0
C 192.168.1.4 is directly connected, Serial1/1
R2#
|
4. Enable OSPF plain text authentication on R1 with the following configurations:
R1(config)#interface serial 1/1
R1(config-if)#ip ospf authentication
R1(config-if)#ip ospf authentication-key cisco
R1(config-if)#exit
|
5. Open debug to observe system prompt after configuration
00:30:33: OSPF: 192.168.1.5 address 192.168.1.2 on Serial1/1 is dead
00:30:33: OSPF: 192.168.1.5 address 192.168.1.2 on Serial1/1 is dead, state DOWN
00:30:33: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial1/1 from FULL to DOWN, Neighbor Down: Dead timer expired
00:30:35: OSPF: Rcv pkt from 192.168.1.2, Serial1/1 : Mismatch Authentication type. Input packet specified type 0, we use type 1
00:54:45: OSPF: Rcv pkt from 192.168.1.2, Serial1/1 : Mismatch Authentication Key - Clear Text
|
6. Enable OSPF authentication on R2
R2(config)#interface s1/0
R2(config-if)#ip ospf authentication
R2(config-if)#ip ospf authentication-key cisco
R2(config-if)#exit
R2(config)#exit
|
7. Check debug information and route information of R1.
00:54:55: OSPF: 2 Way Communication to 192.168.1.5 on Serial1/1, state 2WAY
00:54:55: OSPF: Send DBD to 192.168.1.5 on Serial1/1 seq 0x2154 opt 0x42 flag 0x7 len 32
00:54:55: OSPF: Rcv DBD from 192.168.1.5 on Serial1/1 seq 0x182 opt 0x42 flag 0x7 len 32 mtu 1500 state EXSTART
00:54:55: OSPF: NBR Negotiation Done. We are the SLAVE
00:54:55: OSPF: Send DBD to 192.168.1.5 on Serial1/1 seq 0x182 opt 0x42 flag 0x2 len 152
00:54:55: OSPF: Rcv DBD from 192.168.1.5 on Serial1/1 seq 0x183 opt 0x42 flag 0x3 len 152 mtu 1500 state EXCHANGE
00:54:55: OSPF: Send DBD to 192.168.1.5 on Serial1/1 seq 0x183 opt 0x42 flag 0x0 len 32
00:54:55: OSPF: Database request to 192.168.1.5
00:54:55: OSPF: sent LS REQ packet to 192.168.1.2, length 60
00:54:55: OSPF: Rcv DBD from 192.168.1.5 on Serial1/1 seq 0x184 opt 0x42 flag 0x1 len 32 mtu 1500 state EXCHANGE
00:54:55: OSPF: Exchange Done with 192.168.1.5 on Serial1/1
00:54:55: OSPF: Send DBD to 192.168.1.5 on Serial1/1 seq 0x184 opt 0x42 flag
R1#0x0 len 32
00:54:55: OSPF: Synchronized with 192.168.1.5 on Serial1/1, state FULL
00:54:55: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial1/1 from LOADING to FULL, Loading Done
00:54:56: OSPF: Build router LSA for area 1, router ID 10.1.2.1, seq 0x8000000C
R1#show ip route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 2 subnets
O IA 172.16.1.0 [110/193] via 192.168.1.2, 00:01:53, Serial1/1
O IA 172.16.2.0 [110/193] via 192.168.1.2, 00:01:53, Serial1/1
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback0
C 10.1.1.0 is directly connected, Loopback1
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:01:53, Serial1/1
C 192.168.1.0 is directly connected, Serial1/1
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:01:53, Serial1/1
R1#
|
8. Configure key interface authentication based on MD5 as follows. Please check by yourself after configuration, we will not repeat confirmation here.
R1(config)#interface serial 1/1
R1(config-if)#ip ospf authentication message-digest
R1(config-if)#ip ospf message-digest-key 1 md5 cisco
R1(config-if)#exit
R1(config)#
|
R2(config)#interface serial 1/0
R2(config-if)#ip ospf authentication message-digest
R2(config-if)#ip ospf message-digest-key 1 md5 cisco
R2(config-if)#exit
R2(config)#
|
9. NO the plain text configured before or the interface authentication. Check routing table of R1 and confirm OSPF protocol is processing normally:
R1#show ip route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 2 subnets
O IA 172.16.1.0 [110/193] via 192.168.1.2, 00:00:05, Serial1/1
O IA 172.16.2.0 [110/193] via 192.168.1.2, 00:00:05, Serial1/1
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback0
C 10.1.1.0 is directly connected, Loopback1
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:00:05, Serial1/1
C 192.168.1.0 is directly connected, Serial1/1
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:00:05, Serial1/1
R1#
|
10. Enable area plain text authentication on R1 with the following configuration:
R1(config)#router ospf 1
R1(config-router)#area 1 authentication
R1(config-router)#exit
R1(config)#interface serial 1/1
R1(config-if)#ip ospf authentication-key cisco
R1(config-if)#exit
R1(config)#exit
|
11. after configuration on R1. Wait for a minute and we will see the following information on R1:
01:10:25: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial1/1 from FULL to DOWN, Neighbor Down: Dead timer expired
|
The status is DOWN because R2 is not configured correct authentication. Meanwhile check routing table of R1, and find that the route that has learnt before is lost.
R1#show ip route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback0
C 10.1.1.0 is directly connected, Loopback1
192.168.1.0/30 is subnetted, 1 subnets
C 192.168.1.0 is directly connected, Serial1/1
R1#
|
12. Enable area plain text authentication on R2, with the following configuration:
R2(config)#router ospf 1
R2(config-router)#area 1 authentication
R2(config-router)#exit
R2(config)#interface serial 1/0
R2(config-if)#ip ospf authentication-key cisco
R2(config-if)#exit
|
13. After configuring OSPF area plain text authentication on R2, it will prompt on R1 the following message:
01:15:35: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.1.5 on Serial1/1 from LOADING to FULL, Loading Done
|
This shows that OSPF authentication succeeds now, and R1 has learnt route of other areas. The routing table shows as follows:
R1#show ip route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 2 subnets
O IA 172.16.1.0 [110/193] via 192.168.1.2, 00:01:19, Serial1/1
O IA 172.16.2.0 [110/193] via 192.168.1.2, 00:01:19, Serial1/1
10.0.0.0/24 is subnetted, 2 subnets
C 10.1.2.0 is directly connected, Loopback0
C 10.1.1.0 is directly connected, Loopback1
192.168.1.0/30 is subnetted, 3 subnets
O IA 192.168.1.8 [110/192] via 192.168.1.2, 00:01:19, Serial1/1
C 192.168.1.0 is directly connected, Serial1/1
O IA 192.168.1.4 [110/128] via 192.168.1.2, 00:01:19, Serial1/1
R1#
|
14. The following is an example of configuring key area authentication based on MD5. Please conduct self-check after configuration, because we will not repeat confirmation here:
R1(config)#router ospf 1
R1(config-router)#area 1 authentication message-digest
R1(config-router)#exit
R1(config)#interface serial 1/1
R1(config-if)#ip ospf message-digest-key 1 md5 cisco
R1(config-if)#exit
R1(config)#
|
R2(config)#router ospf 1
R2(config-router)#area 1 authentication message-digest
R2(config-router)#exit
R2(config)#interface serial 1/0
R2(config-if)#ip ospf message-digest-key 1 md5 cisco
R2(config-if)#exit
R2(config)#
|
15. Configure instance of changing MD5 key; this configuration is mainly used to discard old key, and enable new key (also used for area MD5 authentication)
R2(config)#interface serial 1/1
R2(config-if)#ip ospf authentication message-digest
R2(config-if)#ip ospf message-digest-key 1 md5 cisco1
R2(config-if)#ip ospf message-digest-key 2 md5 cisco2
R2(config-if)#exit
R2(config)#exit
|
16. Lab finished.
Hope to helpful for you!
|
